
G-Suite becomes Google Workspace – What’s the difference?
March 4, 2021
Black Friday Luxembourg: how to find the good deals?
November 18, 2021
Phishing is a malicious practice that everyone – companies and individuals – can fall victim to if they are not careful. It is important not to minimize the potential consequences of these practices and to know how to detect and protect oneself from them. This is what we propose to explain in this article.
How to detect a phishing attempt?
Deceptive phishing is the most common technique. The process consists of copying the visual identity used by well-known companies (banks, telephone operators, delivery services, etc.) in their e-mails, and sending their customers false e-mails whose title and content create a sense of urgency in order to frighten them and persuade them to react quickly to an order.
Let’s take as an example this concrete case that recently happened to our partner EuroDNS (domain name provider and web host located in Luxembourg) and let’s unravel the technique used by the hackers and see how to flush out the scam.
1 – The title of the e-mail.
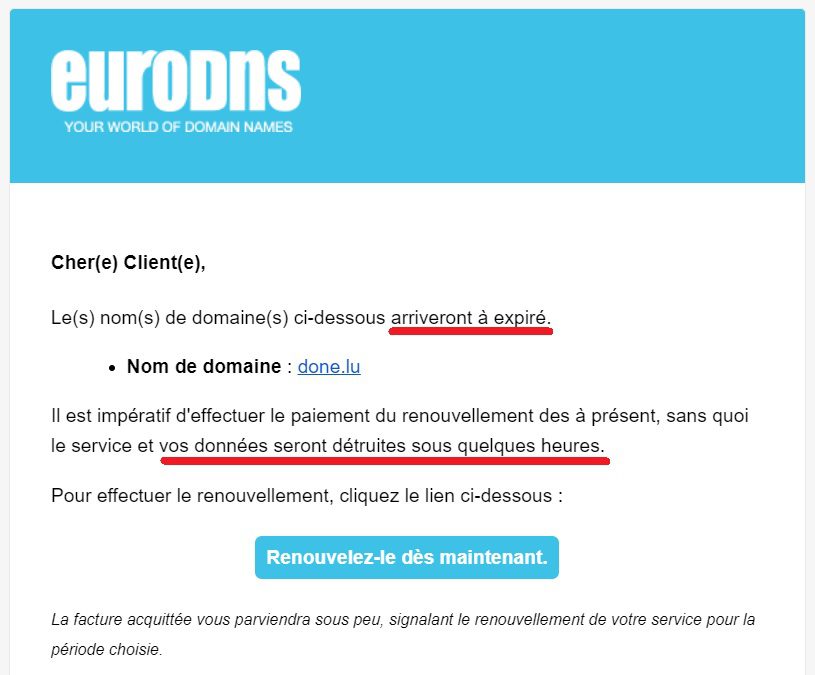
It all starts with the reception of a message on our company email address with the following title (in french):

We can see that the sender’s name has been correctly imitated. On the other hand, the title: “has expired” (“à été expiré”), which contains two mistakes in three words, immediately raises the alarm. Knowing the seriousness of EuroDNS, this kind of error disqualifies this type of email from the start. The reaction to have here is to report this mail as spam and to put it in the trash immediately. But, that day, mechanically, and without paying attention, we opened it.
Please note that simply opening this kind of mail does not have any consequences, unless you are fooled and follow the instructions of the sender.
2 – The content of the e-mail.
Let’s see what our dear sender has to tell us:
At first glance we see that the logo is indeed that of EuroDNS and that the layout of the document corresponds to that of the emails they send to their customers.
On the other hand, once again the ortography and the syntax only confirm that this is indeed a phishing attempt. Beware, however, that these gross errors tend to become less frequent, as hackers are making efforts to make their e-mails more and more credible.
And bim! What had to happen happened, our correspondent tells us to give him money, and immediately. Otherwise, we will be exposed to serious consequences: “your data will be destroyed within a few hours” (“vos données seront détruites sous quelques heures”). Your usual provider certainly never uses this kind of practice.
Let’s face it, someone who is misinformed or acts in haste could easily be fooled. After all, although we are regularly subjected to this kind of email, we opened it mechanically without paying too much attention to it.
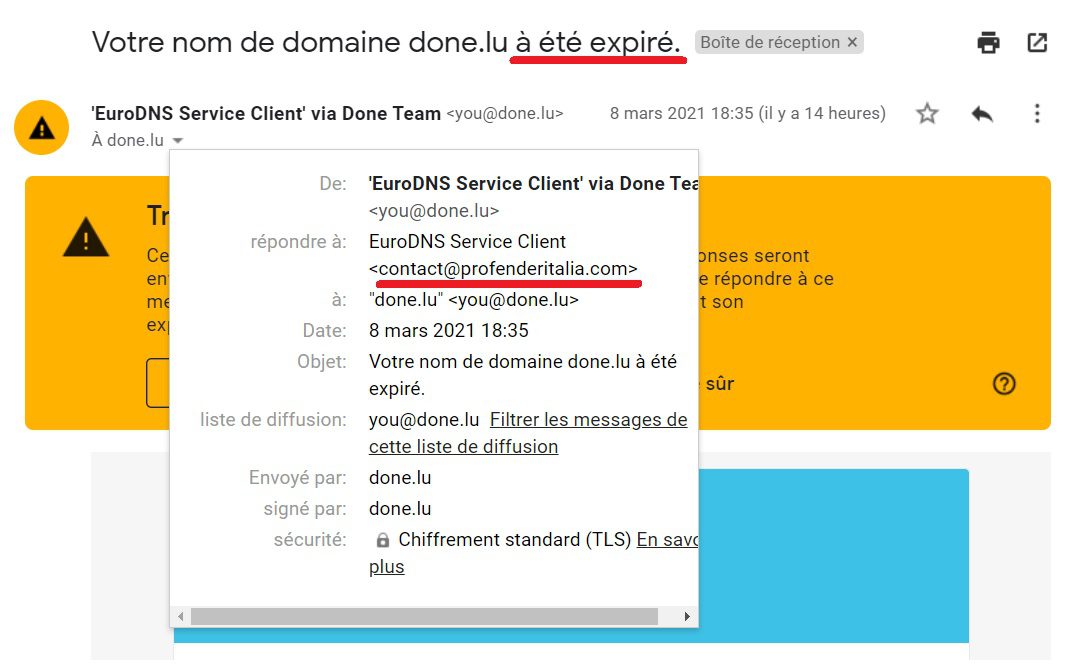
3 – The sender’s address.
By displaying the details of the e-mail it is easy to see that it is not an address that corresponds to the identity of the supposed sender. However, be careful, some imitations can be confusing by repeating the number of consonants or by adding numbers, for example : @carreffourr.com, banque-BIL25.com…
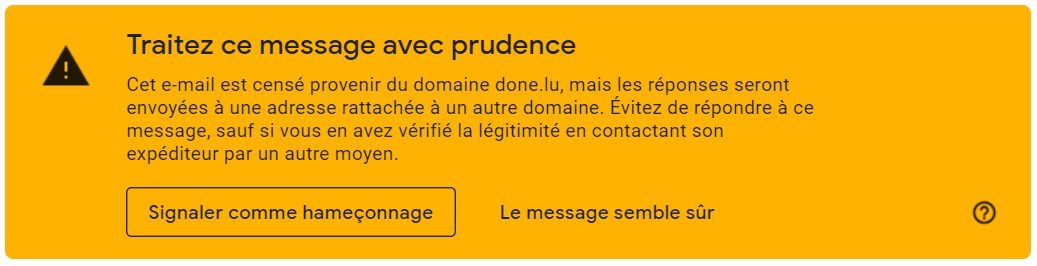
In this case, the Google Spam detector had identified the Phishing attempt, hence the interest in reporting this kind of message so that the warning is propagated as quickly as possible.
Other examples of phishing.
We have mentioned here the case of one of our suppliers but many other scenarios exist. This is the case of newsletters that imitate the identity of a home delivery service. They tell you that your parcel is blocked at customs and that it cannot be delivered without the payment of customs fees, often modest, in the order of a few euros as you can see in this example. This type of scam can also take place via SMS.
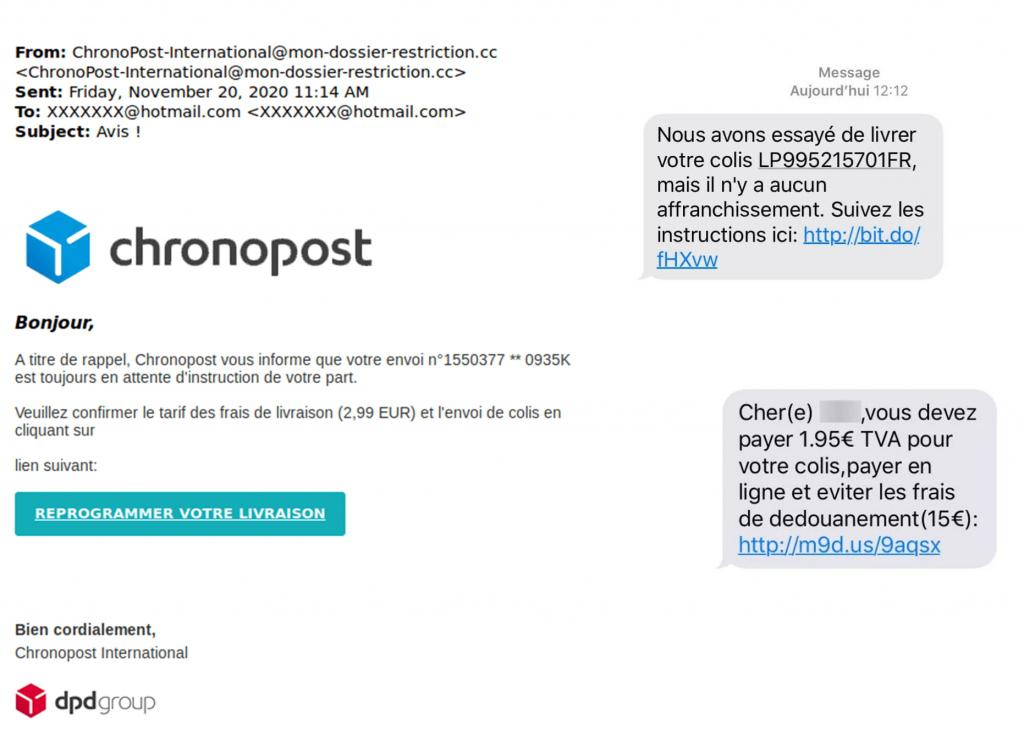
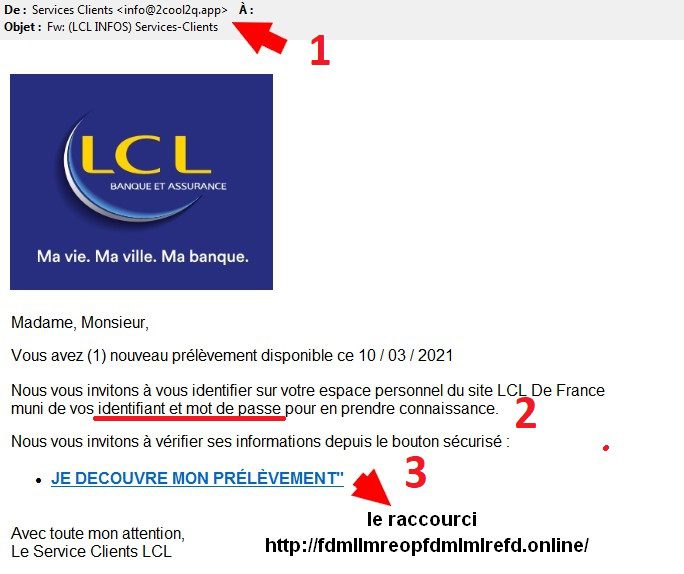
Others adopt the identity of your bank and ask you to click urgently on a link for a reason invented for the occasion. If you click on it, you will be directed to a page where you will be asked for your login and password. We let you imagine the consequences if you were not careful. No organization has the right to ask you for your credit card code, your access codes and passwords. The example below offers a good summary of these identity theft attempts:
- The e-mail address of the sender does not correspond at all to the bank’s corporate name.
- Your bank, like any other company, has no right to make this type of request (asking for login and password).
- The link behind “I discover my direct debit” smells of deception.
Sometimes the message seems to come from a friend – who is asking you to get access to his account – contact him by another means than this email address to make sure that it is really him. By the way, this friend will surely have been the victim of a phishing attempt that will have achieved its goal.
How to react in case of a phishing attempt?
1 – Ask yourself if this e-mail is really intended for you, does it mention a file or an invoice that speaks to you?
2 – Check the spelling and syntax, both in the title and in the content of the e-mail.
3 – Do not click on the link or button that prompts you to take an action (Pay now, Download the attachment, Renew your subscription…)
4 – Check the links in the email. Place the mouse over the link to display the complete link (this manipulation is not possible from a smartphone). Does it point to a legitimate site? Beware of fake domain names that imitate the address of a known website.
5 – Check the sender’s email. Do it scrupulously because it can sometimes happen that the e-mail address of the sender imitates rather well that of a real company.
6 – Do not open or download any attachments, even if the title of the document seems plausible or inciting.
7 – Report it as spam.
8 – Place the e-mail in the trash and delete it. And if you still have any doubts, go directly to the website of the company that the e-mail is trying to abuse – without using the link in the suspicious e-mail, of course – and report the suspicious messages and sites to the companies whose identity has been impersonated.
You can also report these actions to the authorities.
In France: Report fraudulent emails to https://www.signal-spam.fr/ and suspicious SMS to 33700.
In Belgium: Report suspicious emails and SMS to suspect@safeonweb.be
In Luxembourg: the Govcert website informs you about the main past and current phishing attempts: https://www.govcert.lu/
In other countries: The local authorities who are taking care of phishing atempts.
Conclusion.
Always be on your guard!




